CHAPTER VI
HOW TO ENCRYPT YOUR ENTIRE LIFE
“Connected with the Past” by Federico Uribe. 2012. Electric cables on canvas.
Andy Grove was a Hungarian refugee who escaped communism, studied engineering, and ultimately led the personal computer revolution as the CEO of Intel. He died earlier this year in Silicon Valley after a long fight with Parkinson’s disease.
When one of the most powerful people in the world encourages us to be paranoid, maybe we should listen.
And Grove isn’t the only powerful person urging caution. Even the director of the FBI — the same official who recently paid hackers a million dollars to unlock a shooter’s iPhone — is encouraging everyone to cover their webcams.
But you obey the law. What do you have to worry about? As the motto of the United Kingdom’s surveillance program reminds us, “If you’ve got nothing to hide, you’ve got nothing to fear.”
Well, law-abiding citizens do have reason to fear. They do have reasons to secure their devices, their files, and their communications with loved ones.
“If one would give me six lines written by the hand of the most honest man, I would find something in them to have him hanged.” — Cardinal Richelieu in 1641
In this article, I will show you how you can protect yourself by leveraging state-of-the-art encryption. In a single sitting, you can make great strides toward securing your privacy.
Common sense security for everyone
To be clear, everything I recommend here is 100% free and 100% legal. If you bother locking your doors at night, you should bother using encryption.
First, a couple definitions. When I use the term “attacker” I mean anyone trying to access your data whom you haven’t given express permission to — whether it’s a hacker, a corporation, or even a government.
And when I use the terms “private” or “secure”, I mean reasonably so. The reality is that — as long as humans are involved — no system will ever be 100% private or 100% secure.
As long as your phone, computers, and accounts are sufficiently protected, their contents will remain an “encrypted lump” and there’s not much anyone — regardless of how powerful they are — can do about it.
Use two-factor authentication on your inbox
Your inbox is the skeleton key to your life. If an attacker compromises it, they can not only read your emails, they can use it to reset your passwords for pretty much anything. This includes social media accounts and even bank accounts.
The simplest thing you can do to dramatically improve your personal security is to turn on two-factor authentication on your inbox.
Basically, two-factor authentication is a second layer of security when signing in. It usually involves receiving a text message with a special code whenever you sign into your account.
Two-factor authentication substantially reduces the likelihood of your inbox getting hacked.
Encrypt your hard drive
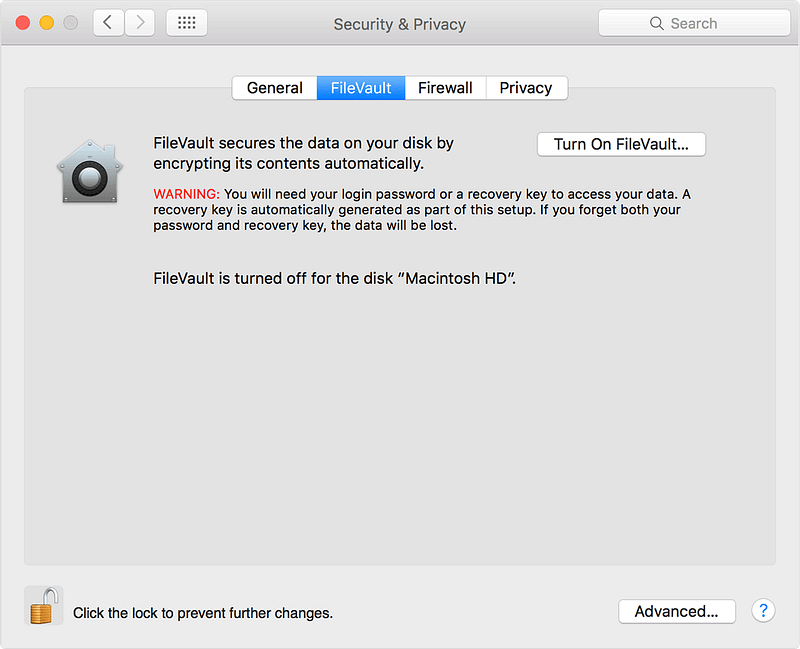
Both Windows and MacOS have built-in full-disk encryption. You just need to turn it on.
Turn on your phone’s password protection
Thumbprint identification is better than nothing, but it’s often not enough.
The fifth amendment (against self-incrimination) allows you to keep your password secret. But a court can compel you to unlock your phone with your thumbprint.
Also, you can’t exactly change your thumbprint after an attacker gets ahold of it.
An attacker will usually get 10 tries before your phone will completely lock them out. So if your 4-digit password is one of these common ones, change it.
1234 9999 1111 3333 0000 5555 1212 6666 7777 1122 1004 1313 2000 8888 4444 4321 2222 2001 6969 1010
Pro Tip: if you insist on enabling thumbprint identification for convenience’s sake, and are ever arrested, immediately power off your phone. When the authorities turn your phone back on, they won’t be able to unlock it without your password.
Use different passwords for each service.
Passwords are inherently insecure.
Mark Zuckerberg used the password “dadada” on his LinkedIn account. Earlier this year, when hackers released 117 million email-password combinations, his was among them. Hackers were then able to use his email and password to gain access to his Twitter and Pinterest accounts.
Don’t use the same password more than one place. Of course, remembering a ton of passwords is a hassle, so use a password manager.
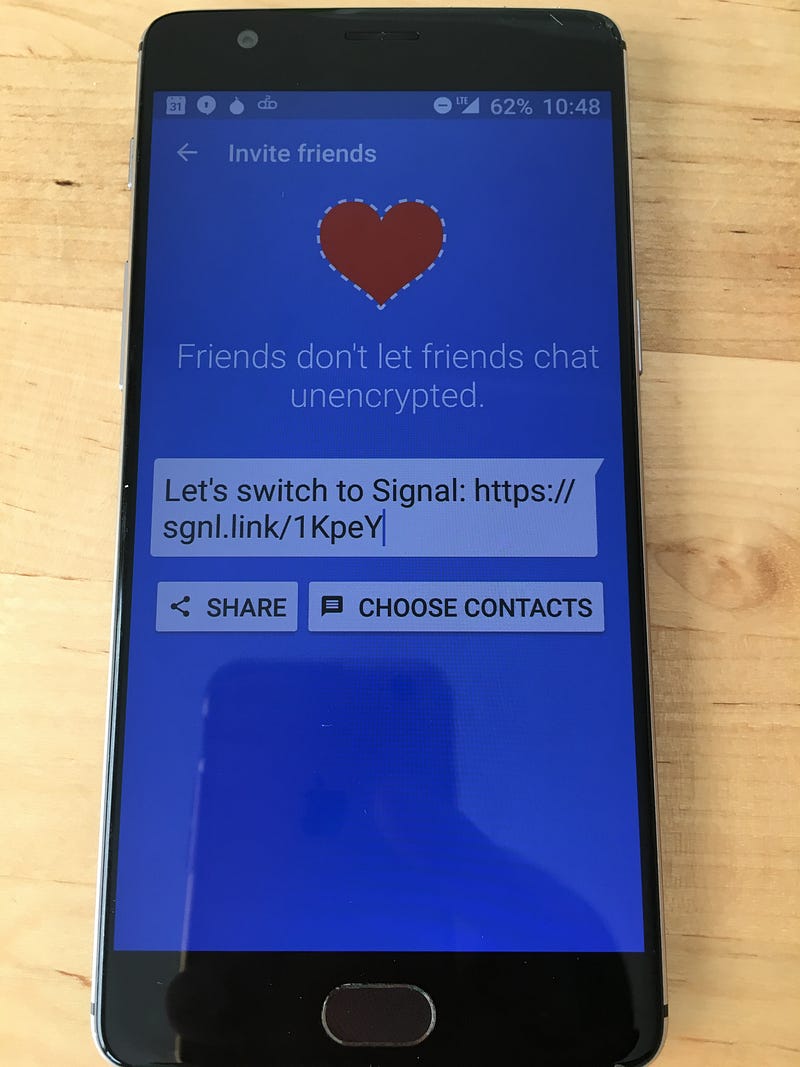
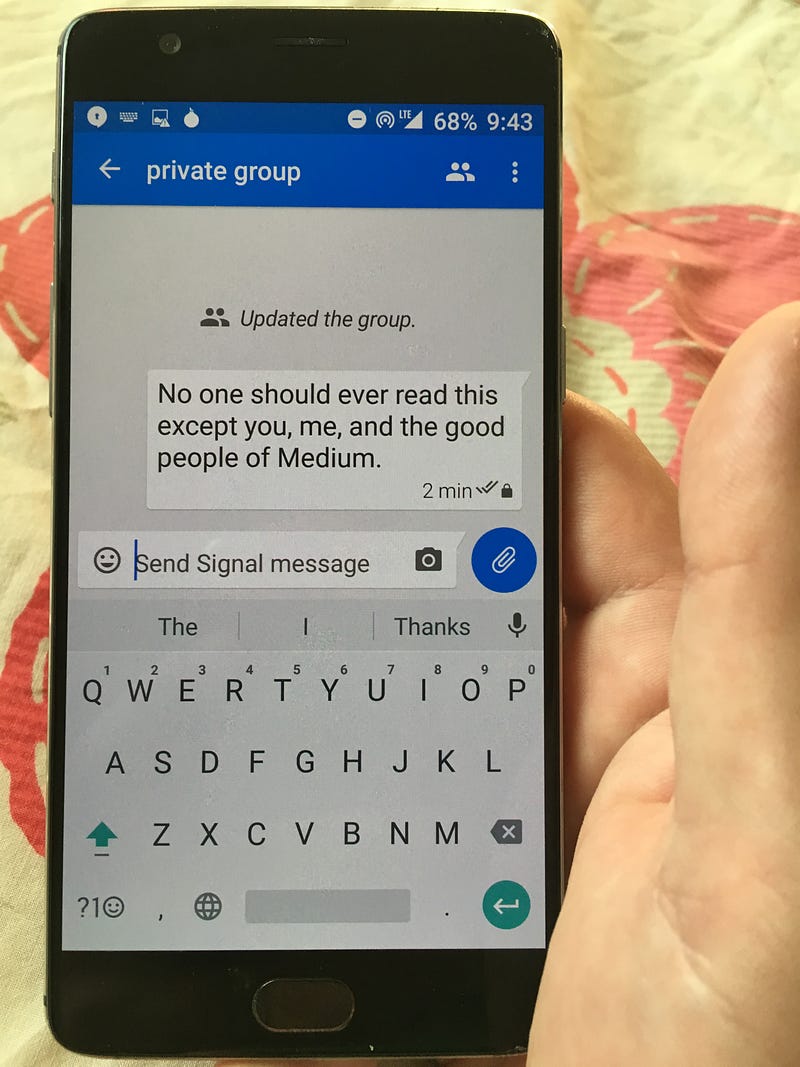
 Send private text messages with Signal
Send private text messages with Signal
Signal is a popular messaging service that got a perfect score from the Electronic Frontier Foundation. You can do all the things you would normally do through text messages, like have group messages and send photos and videos. Except that everything’s encrypted.
Signal is free, open source, and available in iOS and Android app stores. I was able to set it up and start messaging securely with friends and family in less than 5 minutes.
Step #2: Invite friends to install it
Congratulations — you can now talk with your friends and family about whatever you want, and it will be practically impossible for anyone to spy on your conversation.
You can also use Signal to make secure phone calls.
Your browser’s incognito mode isn’t private enough
Even if you use Chrome’s “Incognito Mode” or Firefox’s “Private Browsing”, the following parties will still be able to snoop in on your network activity:
- Internet service providers
- System administrators in charge of the network at your school, workplace, or wherever get online
- Google, or whoever made your browser
Internet Explorer, Safari, Opera, and other browsers are no more private.
If you want reasonably private browsing (no system can ever be 100% secure), you should use Tor.
Browse in private with Tor
Tor stands for “The Onion Router” which is a reference to its use of many onion-like layers to mask network activity. It’s free, open source, and reasonably easy to use.

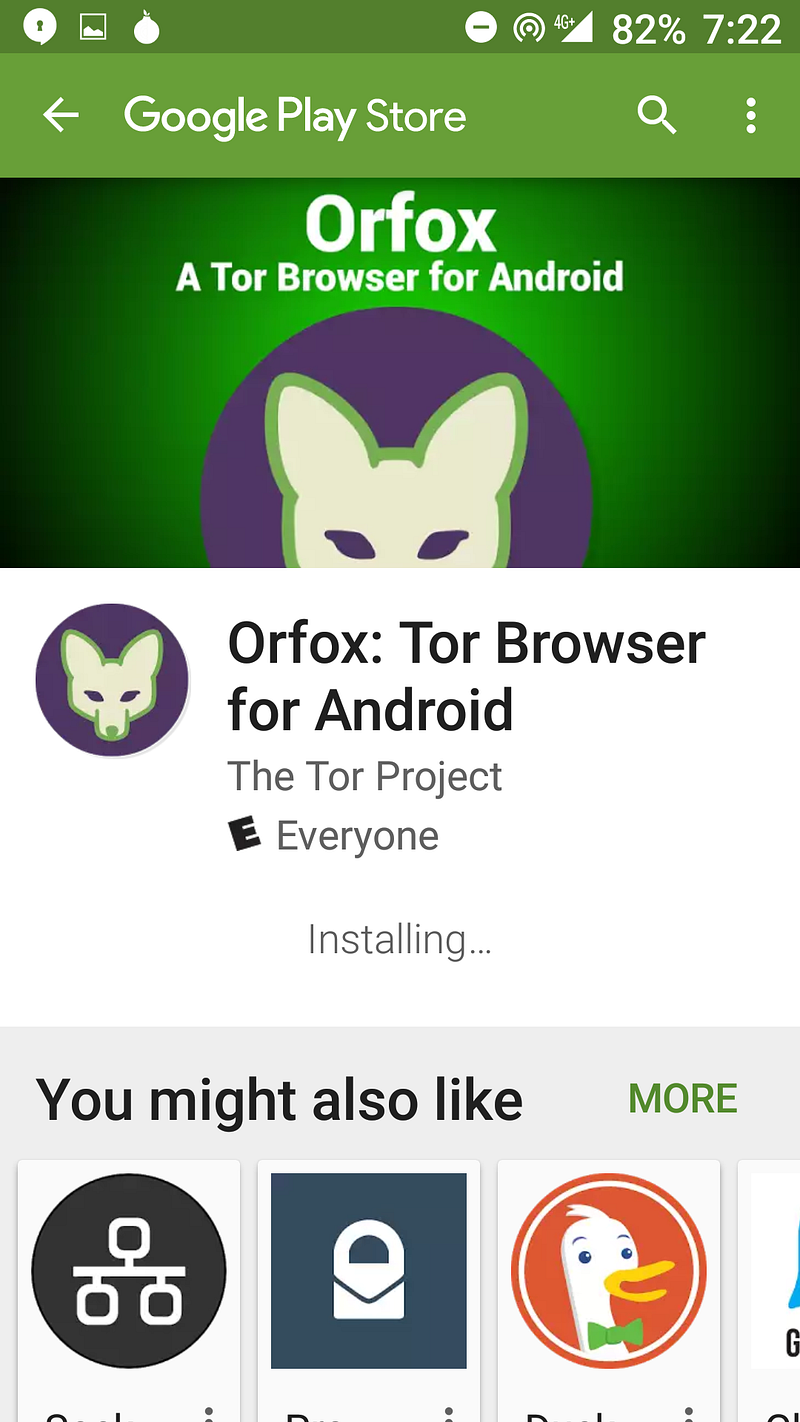 Step #2: Download the Orfox browser
Step #2: Download the Orfox browser
Step #3: Open Orbot
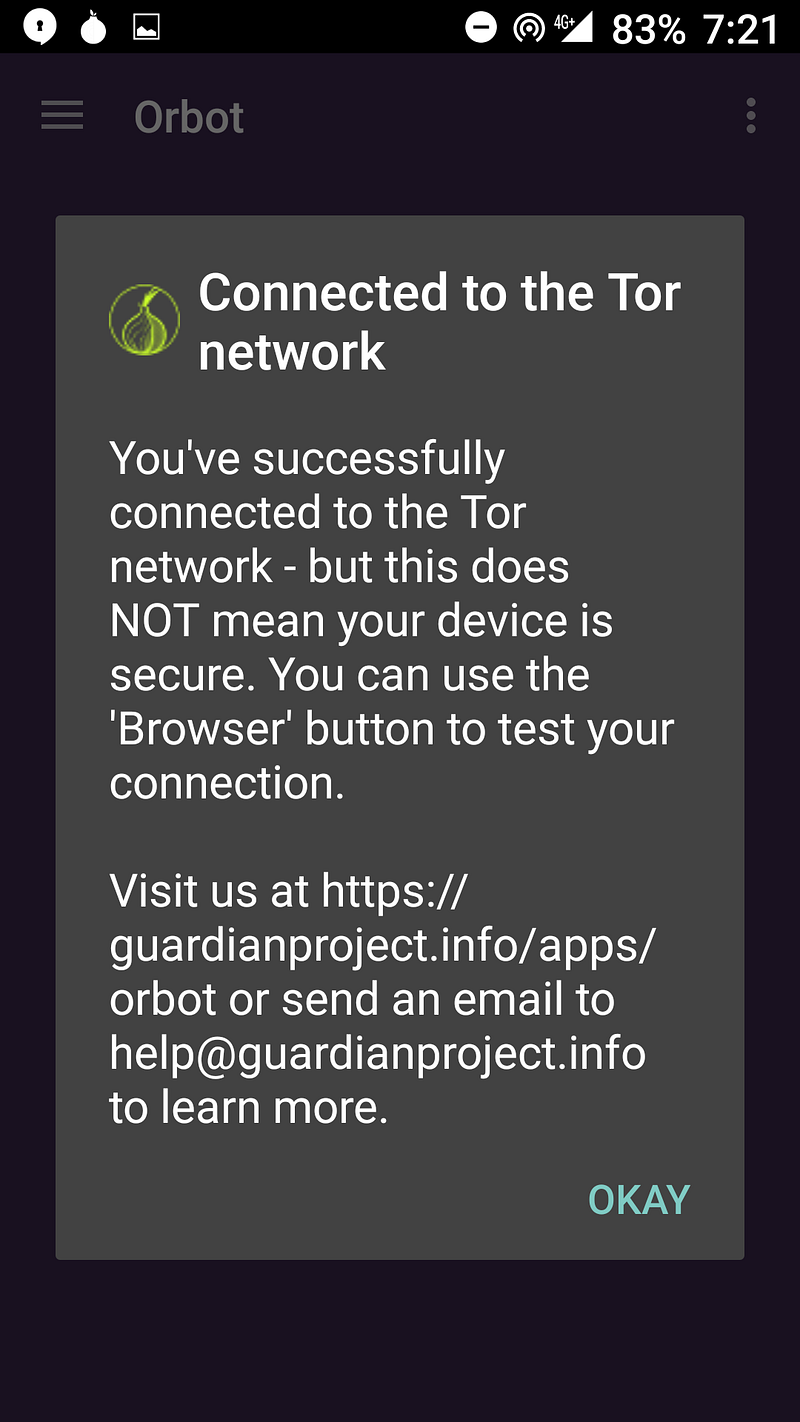
Step #4: Open Orfox
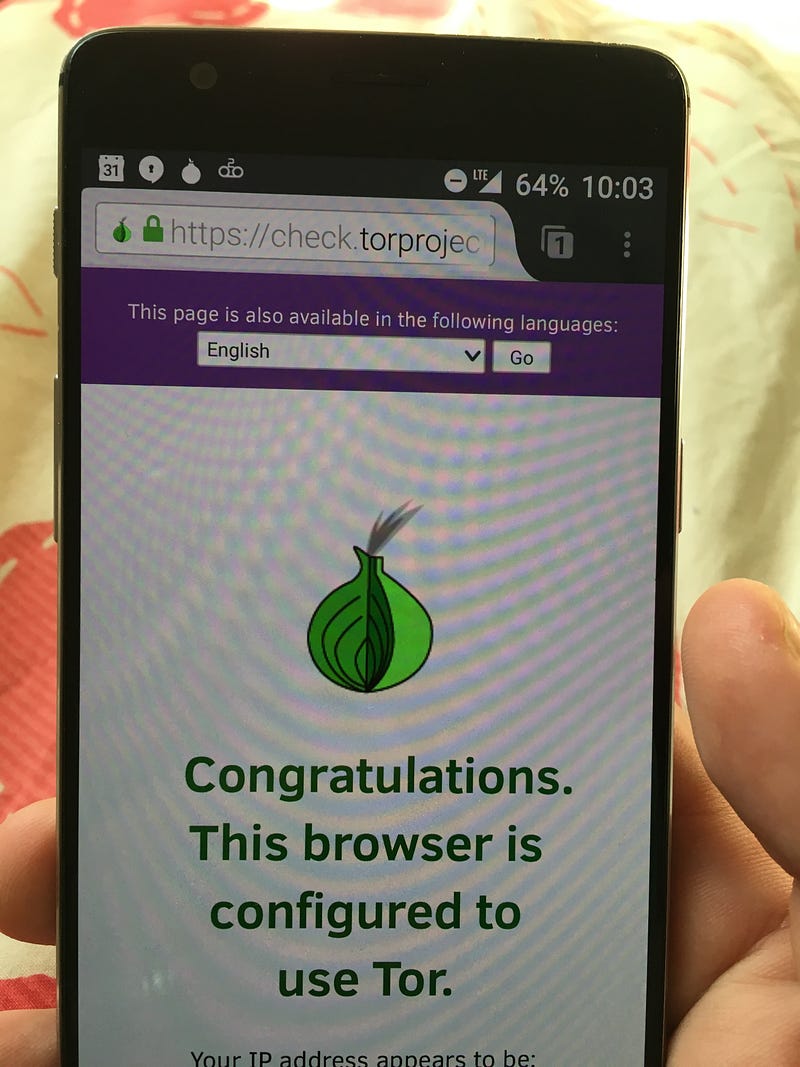
Step #5: Verify it worked
Visit check.torproject.org to verify everything worked. Congratulations — you can now use the internet with peace of mind that it would be extremely difficult for anyone to track you.
Search in private
If Tor isn’t convenient enough for you, you can at least search privately using DuckDuckGo, the search engine that doesn’t track you.
DuckDuckGo doesn’t have all the thousands of engineer-years poured into its search engine that Google has, but it does have a shortcut to get encrypted Google searches when you need them. You just need to prefix your search with !google

Create an anonymous Signal phone number w/ Android
Sometimes you just need an email address and a phone number to do things online. Or maybe you want to ditch you expensive phone plan because your friends and family all smartly use Open Whisper Systems crypto tools. And why not? Signal lets you communicate for free, even to international numbers. This guide will show you:
- how to create a new Gmail address without an existing phone number,
- create a new Google Voice phone number with your new Gmail address,
- and then using your new Google Voice number to setup Signal.
After you complete this guide, your new phone number can send/receive Signal calls and instant messages using Wi-Fi. Persistent SMS capabilities will also be available using Google Voice. Baseband and SIM card exploits will be a thing of the past.
Anonymity is relative in this context. Yes, you’ll be creating a phone number that you’ll probably be giving to other people. Those people will probably know who you are. Pay special attention to step 14. If you follow this guide, you’ll be in a position to maintain communications anonymity in a massive passive-surveillance network.
The following was tested on a Motorola “Moto G” running Android 4.4.4. You will need a laptop to perform the Google Voice aspects of this procedure. Like most guides, you may want to read through the whole thing before starting. Please email or Tweet me if you have any suggestions.
Alternative security
If you just need security and not anonymity, Signal on an iPod Touch is even better.
Guide
1. Obtain an Android phone that was not purchased by you at any retail location. The Nexus phones might be ideal as they typically will not come with a bunch of extra software installed. The Moto E is also a good choice. Craigslist should be fine. Pay with cash. You don’t want any phone device IDs linkable to you (including by way of electronic payment cards and shipping addresses).
1.1. To further distance your connection to device IDs and location-based IPs, take a bus (pay with cash) to a different city than the one you live. Don’t bring any other personal cell phones. Go to a mall and buy a used Android from one of the kiosks. Follow the steps in this guide while you are located in that city. Do nothing else in the city; don’t go and get your face on a bunch of cameras, and don’t pay for things with debit/credit cards.
2. Go to a public library or coffee shop with free Wifi with your Android, laptop, and Tails Linux (USB or DVD). Make sure it’s a place that you’ve never been to and one which you’ll never return to. Order a coffee with cash, be nice, and avoid interacting with people.
3. Remove any SIM cards from the Android. Turn on then restore the Android to factory defaults. Skip all activation settings and enable Airplane Mode as soon as possible. Disable or uninstall all possible apps that aren’t needed, especially ones that sync. You need, at a minimum, Google Play Store, Google Play Services, and Google Services Framework. With Airplane mode still enabled, turn on Wi-Fi and connect.
4. Open Google Play Store. Create a new Gmail address when Android prompts you to log in. Don’t use any words or phrases in either your email address or your password that you’ve used before. And don’t use a password that you’ve ever used before.
5. Using your laptop, boot up Tails Linux. Open the “insecure” browser that is not Iceweasel to log in to your Gmail address. Do not use Iceweasel or Tor, Google will lock you out of the new account, and you’ve already shown Google where you are in steps 3 and 4.
5.1. Make sure you do not proceed if you are prompted to accept bogus SSL/TLS certificates.
5.2. Booting up Tails has two advantages despite not using Tor: 1) the Wifi MAC address is spoofed, and 2) when you shut down your laptop, no history is saved. Do not use Tor to log in to your Google account until after you have two-factor authentication set up.
5.3. If you ever need to enter an alternate email address, simply open the Gmail Android app and create a new address. You can use it as the backup for your new primary address.
6. Use your Android to download “Talkatone“, a free VoIP Android app that gives you a temporary phone number. You will use it to receive phone calls over Wi-Fi. Register for a new account for a new number using your new Gmail address. You may need to search various area codes to find one that has numbers available.
7. Log into google.com/voice with Tails’ insecure browser. Enter your Talkatone phone number and receive its call to verify the number. Go into settings and verify that both “Receive text messages on this phone” and “Notify me of new voicemails via text” are checked. Turn Call Screening off in the Calls tab.
7.1. You can stop here if you don’t need Signal. You may only need a WiFi connected Android with Google Voice to privately receive access tokens via SMS.
8. Never use this phone from any place you routinely go (anchor points) unless you are behind Tor. See (*) below.
Signal configuration and Android configuration
9. Download “Signal” and register it with your Google Voice number. The SMS verification will fail. Wait and then verify via phone call. Your temporary Talkatone number will receive a call, so prepare to write down or remember the six-numeral verification code. Enter the code to verify Signal.
10. Encrypt the phone (Settings > Security > Encrypt phone).
11. Only use this device for Signal (and maybe Google Authenticator, see #13) from now on to minimize its exposure. Especially do not use apps that have in-app ads. Uninstall Talkatone. Uninstall or disable all web browsers. Uninstall or disable all Google apps and services except Google Play Services (and maybe Google Authenticator, see #13). You will need to enable Google Play Store again at some point to keep apps updated, but only at another random, public Wifi location. Always keep all syncing disabled, you do not want Google to have your contacts.
11.1. “NetGuard” may be a useful solution for keeping network activity minimized.
12. Open Signal. Disable SMS/MMS to both Signal users and non-Signal users in settings. Require password access to Signal by turning on “Enable passphrase” to further harden the message database in addition to adding another layer of defensive security (shoulder surfing for the phone access passphrase is easy). Set a low “Timeout interval”.
12.1. When preparing to IM someone with Signal, be sure to first add a contact in your Contacts. When you’re looking at your Signal contact list (or lack thereof), tap the refresh symbol to force a refresh. Now you should be able to see Signal users that can receive your IMs.
13. Using the “Google Authenticator” Android app, enable two-factor authentication (2FA) for access to your new Gmail. If an attacker can get into your Gmail accounts, an attacker could register your number with a new device and deny you the ability to communicate with Signal. When configuring your new Google account, you can now use your new Google Voice number as a verification phone number. Immediately configure 2FA with only Google Authenticator and Google Voice as a backup.
13.1. To further compartmentalize, put your Google Authenticator tokens on a separate device — Preferably one that remains in Airplane Mode all the time.
14. Tell people that you communicate with, not to save your number with any personally identifiable name. The apps they use–like Facebook or their Google Contacts sync–will betray your privacy by recording their contact list, forever creating the digital record of your name with your new number. You can also change the name that appears with your caller identification on the receiver’s side of the call. Use this feature by creating an alias for your name. For example, make the caller ID show “Pizza Hut” or “Marlo Thomas” as the caller name. That way, when the person you are calling receives your call, his or her contact list will simply show this name, and ask the person not to change it.
15. Log into google.com/voice with Tails’ insecure browser on your laptop and disable forwarding to your former Talkatone number. Or alternatively, use Tails’ Iceweasel (Tor) and test access now that 2FA is configured.
Optionally…
 16. Physically remove the phone’s microphone and cameras; if possible, the accelerometer too. Rely on a corded headset when communicating with Signal (voice). Don’t leave the headset plugged in when not in use.
16. Physically remove the phone’s microphone and cameras; if possible, the accelerometer too. Rely on a corded headset when communicating with Signal (voice). Don’t leave the headset plugged in when not in use.
16.1 If an attacker is able to compromise your device, you do not want them to be able to hot-mic your Android or take pictures/video of your environments.
This is an iPhone with its microphone and front camera removed.
Root?
There are pros and cons to rooting your phone. Rooting might make the job of targeted attacker much easier. Should you root for more control (creating new vulnerabilities) or simply hope that Airplane Mode is doing what it promises when you are carrying your phone with you at anchor points?
(*) There are several options for getting Signal to work with Tor, but the downside is that only Signal IMs will work, not Signal voice calls. One option is to create a wireless access point for your anchor points that force all traffic over Tor, which does not need root, like P.O.R.T.A.L.. It also may be possible to leverage another Android phone that is already rooted and running Orbot to tether through. And again, InvizBox and Anonabox are simple solutions, but you have to buy them online and have them shipped somewhere, creating a lot of metadata. Lastly, there is the option of rooting and using Orbot to proxy local Android traffic.
Mission Impossible Android Hardening on Github, previously on the Tor Project blog, goes into good detail on how to root your Android device and attempt to delete the Android baseband firmware partition.
Once your Android is rooted, you would need to install a 3rd-party ROM that does not have any Google services pre-installed. Then you’d have to find the Signal APK online (plus verifying their hashes) and manually install the apps you need. There are some interesting, unsupported ways to get and use Signal on an Android. Google Cloud Messaging (GCM) is required unless another service pretends to be GCM.
Ideally you’d use an iptables-based firewall to prevent any apps or services using any network interface except Signal and Orbot. You would also need to find a different long-term VOIP provider (to receive phone calls and SMS) since you wouldn’t be setting up a Gmail or Google Voice in this scenario.